Azure Governance Starter – Part 1: Understanding Fundamentals, Risks, and Frameworks
Why governance is more than just policies, what risks arise without it, and how the Microsoft Cloud Adoption Framework (CAF) and Well-Architected Framework (WAF) lay the foundation for secure and scalable cloud operations.

Why Cloud Governance Is More Than Just Policies
When getting started with Azure, the focus is often on speed and flexibility. Subscriptions are quickly created, resources provisioned, workloads migrated. But without structured governance, security risks, cost explosions, and operational problems inevitably occur. Governance is not a retroactive control mechanism; it is the foundation of sustainable cloud operations. Microsoft offers two structured guides—Cloud Adoption Framework (CAF) and Well-Architected Framework (WAF)—to strategically, operationally, and technically embed governance.
Whereas traditional IT infrastructures were highly centralized in the past, cloud platforms like Azure bring about a democratization of infrastructure. Developers, project teams, or business units can provision resources independently. This enables flexibility, but also introduces potential chaos. This is where governance comes into play.
It’s important to distinguish between:
- Governance: Defining and enforcing policies, standards, and structures (What is allowed, how, where, and by whom?)
- Management: Operational management and monitoring of existing resources (How are resources operated and monitored?)
- Compliance: Ensuring regulatory and legal requirements (Are we auditable, compliant, and documented?)
Governance is thus the strategic umbrella that structures both management and compliance.
Real-World Problems Without Governance
Many companies that start without a governance model encounter the following challenges within just a few months:
- Security incidents due to publicly accessible resources like Storage Accounts or Key Vaults
- Cost explosions due to lack of shutdown automation, reservations, or resource control
- Regional data misplacement, e.g., storage of personal data in third countries
- Unclear responsibilities: Who can delete what, who is responsible for which costs?
- Unclear architecture: Networks with overlapping IP ranges, fragmented infrastructure, manual deployments
Cloud Adoption Framework (CAF): The Methodological Framework
Microsoft’s Cloud Adoption Framework (CAF) is a comprehensive guide designed to help organizations structure, secure, and business-align their cloud adoption. It targets strategic decision-makers, architects, and platform teams and covers all phases of cloud adoption—from initial strategic planning to continuous operational optimization. Governance is not an isolated element but a cross-cutting theme throughout every phase.
Strategy Phase
In this phase, the business value of cloud adoption is defined. It involves identifying business drivers (e.g., innovation pressure, scalability, cost optimization) and prioritizing cloud initiatives. Stakeholders are involved, KPIs are defined, and the strategic objectives for cloud adoption are documented. The goal is to align cloud adoption with overall business goals.
Mission and Goal Definition: A company-wide cloud mission is formulated that outlines the long-term benefit and role of the cloud. Based on this, measurable goals (KPIs) are defined to guide all further steps. These goals support success measurement and provide transparency to stakeholders.
Business Case Development: Analysis of expected economic benefits from cloud adoption based on concrete use cases. This compares capital expenditures, operational costs, potential savings, and innovation opportunities. The business case serves as a management-level decision basis and evaluates the cloud’s strategic value.
Risk Assessment: Identification of technical, legal, and operational risks associated with cloud migration. This includes data residency, regulatory requirements, technical debt, legacy dependencies, and skill gaps. Risks are categorized, assessed, and mitigated. The goal is early minimization of modernization risks.
Sketching Target Architecture: Creating a high-level vision for the future cloud environment. This includes expected workload types, network segmentation, region strategy, identity model, and on-premises integration. The focus is on strategic vision rather than technical details.
Creating a Stakeholder Map: Systematic identification and analysis of all relevant internal and external stakeholders—business units, IT teams, security, finance, compliance, partners, and regulators. The aim is to clarify expectations, influence, responsibilities, and communication paths.
Establish Strategy Team & Assess Organizational Readiness: A dedicated interdisciplinary strategy team is formed to design and drive the cloud strategy. Organizational readiness is also assessed, including leadership commitment, tech maturity, change agility, and willingness to modernize processes.
Plan Phase
In the Plan phase of the Azure CAF, strategic decisions are turned into a technically and organizationally feasible plan. The existing IT landscape is analyzed in detail, target architectures are refined, and the technical/organizational foundation is laid for implementation.
The goal is to establish a solid starting point for deploying Azure workloads that meet both business and regulatory needs.
Inventorying Applications: All workloads are documented along with dependencies (databases, APIs, systems, identities). Tools like Azure Migrate, Application Insights, or third-party tools help visualize data flows and technical debt. This inventory informs migration decisions and prioritization.
Cloud Readiness Assessment: Each workload is evaluated for continued hosting viability, considering latency, residency, modernization effort, and licensing. Based on this, a Rehost, Refactor, Rearchitect, or Rebuild strategy is selected along with IaaS, PaaS, or SaaS models.
Defining Architecture Principles: Overarching design principles are documented in an architecture guide or cloud strategy paper—covering security, scalability, reusability, automation, and integration. These guide detailed planning in the Ready phase.
Creating a Cloud Roadmap: Based on the inventory, a time- and technology-aligned roadmap for migration and new development is created. This includes migration waves, dependencies, priorities, budgets, training capacity, and external constraints.
Budget & Licensing Planning: Cost estimates for migration, licenses, and operations. Recommendations include Reservations, Savings Plans, and Azure Hybrid Benefit for cost efficiency.
Designing the Management Group Structure: The root structure mirrors the organization. Typical segments include business units, regions, and environments (e.g., prod, test, dev). Subscriptions are assigned accordingly with defined responsibilities. Azure Policy initiatives are used early on to enforce standards like allowed regions, naming conventions, and mandatory cost tags.
Documenting the Subscription Strategy: Each subscription receives a defined role and usage model—RBAC, budget limits, resource quotas, naming conventions—aligned with central policies.
Defining the Operating Model: Decide between centralized, shared, or decentralized models, depending on maturity. Governance, security, and operations are divided between platform and workload teams. A hybrid model is often best.
Building the Governance Team: A dedicated team defines policies, assesses risks, and ensures implementation. It oversees IAM, compliance, policy design, and resource control.
Security Planning (Security by Design): Security is integrated early into all architecture decisions—Zero Trust, IAM (Entra ID), network protection, sensitive data safeguards, monitoring, and threat detection. Collaboration with security/compliance stakeholders is essential.
Tooling Decisions: Define deployment, automation, and monitoring tools—e.g., Azure DevOps, GitHub Actions, GitLab, Bicep, Terraform, Grafana, KQL Workbooks, Azure Monitor.
Organizational Role Definition: Assign clear responsibilities for governance, architecture, security, FinOps, and automation. This ensures lasting adherence to standards, budgets, and security.
This phase concludes with a full planning document reviewed by a governance body (e.g., Cloud Governance Board) to serve as a reference for the Ready phase.
Ready Phase
In the Ready phase, the cloud platform is prepared to be production-ready, secure, and scalable. The goal is to build a robust, maintainable, and compliant base infrastructure that serves as the technical foundation for all future workloads. This phase is crucial because governance, security, and automation are first implemented in practice here.
A central concept is the development of Azure Landing Zones—standardized and reusable infrastructure components such as networking, identities, policies, and monitoring tools. Microsoft provides prebuilt Landing Zone Accelerators, though custom Infrastructure-as-Code (IaC) templates are often needed to meet company-specific requirements.
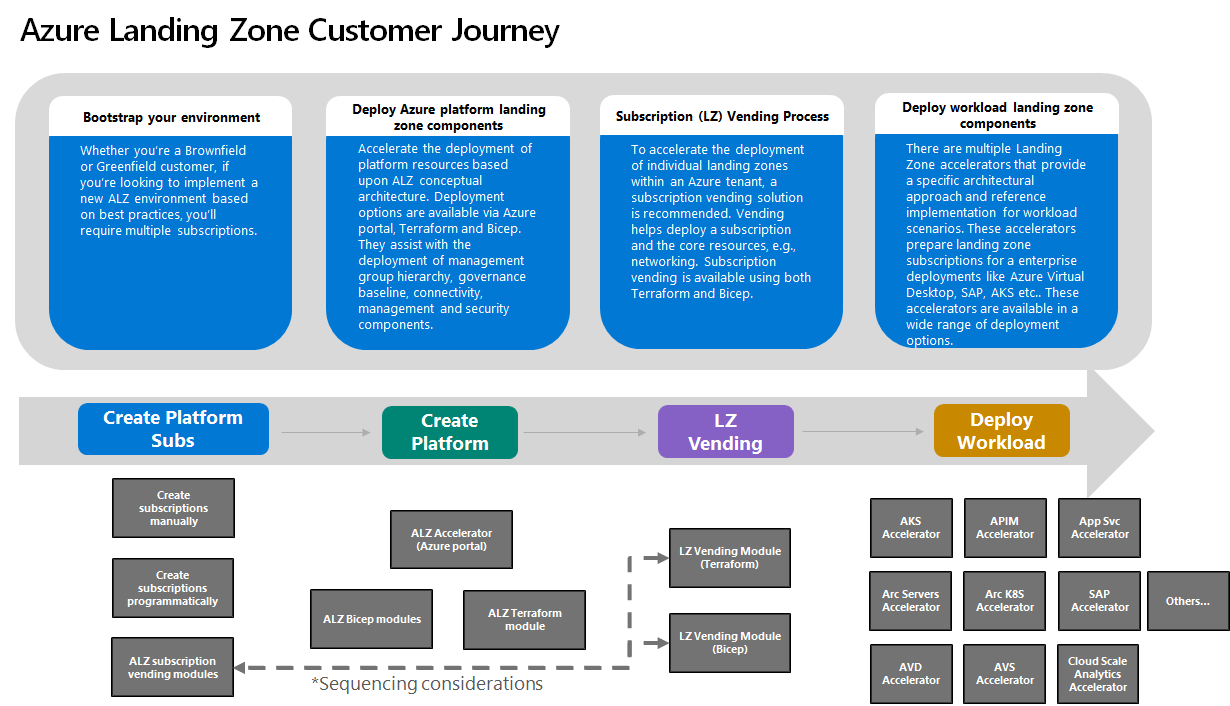
Each Landing Zone can target a department, project, or logical separation. It should include CAF design areas such as Identity & Access Management, Network Design & Connectivity, Resource Organization & Management Groups, Governance & Policies, Security & Protection, Monitoring & Management, Platform Automation (IaC), and Hybrid Connectivity & Integration.
Management Groups & Policies: The previously defined Management Group structure is now implemented in Azure. Associated Azure Policy initiatives like Allowed Locations, Tag Enforcement, and Blueprint Assignment are rolled out—first in Audit mode, then with Deny or Modify effects.
Identity & Access: Entra ID acts as the central identity platform. RBAC is assigned using the CAF RACI model. Privileged Identity Management (PIM), Conditional Access, and Multi-Factor Authentication (MFA) are enabled for privileged accounts. Standard roles and permission groups are deployed automatically.
Tagging Standard & Naming Conventions: Consistent tagging and naming standards are enforced using policies, deployment scripts, and pipelines. Policy violations trigger a defined review and escalation process. Tags are mandatory for governance, automation, and cost allocation.
Network Design & Region Governance: The chosen network architecture (e.g., Hub-Spoke, vWAN) is implemented with DNS, Private Endpoints, VPN Gateways, or ExpressRoute. Only approved Azure regions are allowed for workloads (enforced via Region Governance Policy).
Security Configuration: Azure Defender is activated across all subscriptions and integrated with Microsoft Sentinel or centralized SIEM systems. Ideally, automated vulnerability scanning and alerting are also implemented.
Central Monitoring: Azure Monitor, Log Analytics, and Application Insights are centrally connected across the tenant. Diagnostic Settings are activated automatically via policy on all resources.
Cloud Center of Excellence (CCoE): The CCoE is established as the governance and enablement team. It manages technical standards, publishes reference architectures, oversees policies, trains stakeholders, and moderates the governance process via governance boards.
Onboarding Processes: New projects and teams are onboarded using structured processes—template selection, permission assignments, budget allocation, and policy commitments. The goal is to avoid shadow IT and empower Dev teams for governance compliance.
Backup and Disaster Recovery: Business continuity and DR strategies are integrated, including geo-replication, automated backups, and defined RTO/RPO objectives.
The phase concludes with readiness validation by the Cloud Governance Board using a full CAF Ready checklist to ensure prerequisites for the next "Adopt" phase are met.
Adopt Phase (Migration and Innovation)
The Adopt phase marks the execution of the cloud strategy. Existing workloads are migrated, and new cloud-native apps are developed using the previously established governance and platform standards.
The foundation is the Cloud Adoption Plan, which documents all migration goals, dependencies, strategies, workload priorities, timelines, and success metrics.
Two main scenarios in this phase are:
- Migrating existing workloads: Selecting the right migration strategy (Rehost, Refactor, Rearchitect, Rebuild, Replace, or Retain) based on technical suitability, criticality, and business needs.
- Developing new cloud-native solutions: Building apps with Azure-native services like Functions, App Services, Logic Apps, Event Grid, Cosmos DB, or AKS using modern architecture patterns like microservices or event-driven design.
Planning and Executing Your Migration
Before migration, technical and business dependencies between workloads are identified. These inform the creation of migration waves to avoid bottlenecks and downtime. Each wave groups workloads with shared databases, APIs, identities, or network connections.
Depending on SLA and criticality, different migration methods are used. For non-critical systems, downtime migration may suffice. For high-availability workloads, near-zero-downtime migration is appropriate.
Even with careful planning, switching production systems may lead to short-term downtime due to DNS or public load balancer changes.
Cloud-Native Development & CI/CD
All infrastructure components (e.g., networks, identities, policies) are deployed using IaC via Bicep, Terraform, or ARM templates. Azure Policies and RBAC assignments are versioned, tested, and deployed via pipelines (Policy as Code).
Application deployments are automated using Azure DevOps, GitHub Actions, or GitLab. Pipelines include security checks, policy compliance, and automated tests (e.g., KQL, SonarQube).
Dev teams are trained in DevSecOps practices such as Key Vault secrets management, managed identities, and least privilege. Guardrails like policies blocking public IPs or enforcing encryption ensure security compliance.
Rollback Strategy
Each workload has a rollback plan with defined triggers (e.g., performance drops, error rates). Automated recovery mechanisms are built into CI/CD pipelines. Snapshots, IaC backups, and image rollbacks are regularly tested to ensure recovery readiness.
Operational Handover & Success Measurement
Post-migration, responsibilities are reassigned. Availability, performance, and user feedback are monitored to identify issues. The previously implemented observability measures are leveraged here.
This phase proves whether governance works in practice—not as a blocker, but as an integrated part of the development and operations process. Productivity and security in the cloud emerge when teams are empowered through self-service and automation within a governance framework.
Govern Phase
The Govern phase ensures that all Azure activities are controlled, traceable, and compliant. It involves both technical control and organizational anchoring, focusing on automated enforcement and continuous monitoring.
CAF Governance Strategy follows a five-step cycle:
- Establish a Governance Team
- Assess Cloud Risks
- Document Governance Policies
- Enforce Policies via Technology
- Continuously Monitor and Optimize
Seven core governance areas are defined:
- Security (Access, Identity Protection)
- Compliance (GDPR, ISO 27001)
- Cost Management (Budgeting, Reservations)
- Operations (Change & Incident Management)
- Resource Management (Naming, Tagging, Locations)
- Data Control (Residency, Classification)
- AI Governance (Ethical AI Use, Data Source Control)
Key technical mechanisms include:
Azure Policy & Initiative Definitions: Enforces naming, tagging, regions, resource types, and security rules. Initiative Definitions group policies (e.g., security baseline, cost control). Deny blocks violations; Audit and DeployIfNotExists automate corrections.
Budgeting & Reservations: Azure Budgets define thresholds for subscriptions or resource groups with alerts and automation on overages. Reservations and Savings Plans offer long-term savings.
Access Reviews & PIM: Azure AD Access Reviews periodically check access rights. PIM enables temporary roles with approval workflows and logging—preventing permission bloat and role drift.
Compliance Integration & ITSM Integration: Policy violations and config deviations are analyzed via Azure Monitor, Log Analytics, and Resource Graph. Integration with ITSM tools (e.g., ServiceNow, Jira) ensures ticketing and escalation. Compliance reports (GDPR, ISO) are available via Blueprints or Defender for Cloud.
Role Models & Escalation Paths: Governance defines ownership of policy approvals, cost responsibility, security assessments, and operations. A Governance Board reviews escalations and rollout decisions.
Reporting & Dashboards: Dashboards via Azure Workbooks, KQL, and Power BI visualize policy compliance, costs, security posture, and deployment patterns.
Governance is a dynamic control system, technically scalable and continuously aligned with security, business strategy, and regulation.
Secure Phase
The Secure phase ensures that security is not a one-time task but a continuous, holistic process embedded across all cloud adoption phases. Based on the Zero Trust model, it follows the principles of Assume Breach, Least Privilege, and Explicit Verification.
The goal is to proactively address risks and make organizations resilient to attacks, misconfigurations, and data loss.
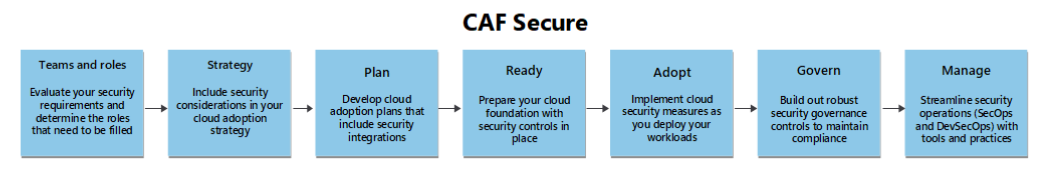
Holistic Security Approach:
Secure addresses security from technical, procedural, and organizational angles. Technical security includes IAM, network protection, workload protection, and end-to-end encryption. On the process side: incident response, security runbooks, and vulnerability management. Organizationally: defined roles, security governance, and continuous training/awareness programs.
CAF recommends treating security as a shared responsibility across all teams, platforms, and lifecycle phases.
Modernizing Security Posture:
CAF Secure aligns with Microsoft’s Zero Trust Adoption Framework and recommends strengthening security iteratively. This includes enabling Multi-Factor Authentication (MFA), Conditional Access, and identity-based access controls.
It also includes integration of Microsoft Defender for Cloud, Entra ID, and Microsoft Sentinel for holistic monitoring and protection. Security baselines and Azure Policy–based compliance automation ensure consistent standards. IaC is recommended to codify security configurations for repeatability, transparency, and automation.
Preparation and Response to Security Incidents:
Organizations must have reliable processes for identifying, evaluating, and responding to security incidents. This includes automated SIEM monitoring (e.g., Microsoft Sentinel) to detect and analyze threats, plus SOAR playbooks for automated responses.
Well-defined escalation paths and incident runbooks, including communication guidelines, ensure effective reactions during incidents. Simulations (e.g., Red Team/Blue Team exercises) help validate and refine incident processes.
Confidentiality, Integrity, Availability:
- Confidentiality: Encryption, access controls, DLP to restrict access to authorized users.
- Integrity: Version control, code signing, tamper protection to ensure data accuracy.
- Availability: Scalable architectures, regular backups, redundancy, and DDoS protection to ensure uptime.
These three principles span the entire CAF and must be embedded in technical and procedural mechanisms.
Maintaining Security Controls:
CAF recommends ongoing assessment and enhancement of security posture. Modern tools like Defender CSPM, Entra Permissions Management, and Secure Score offer centralized visibility into risks and improvements.
Regular security reviews and benchmarks help track progress and compare with industry standards. Security governance teams monitor posture using KPIs like Time-to-Detect or policy compliance rates.
Security Champions within workload teams drive awareness and embed best practices in development workflows.
Manage Phase
The Manage phase of the Azure Cloud Adoption Framework (CAF) represents the operational control loop of cloud governance and operations. It ensures that Azure environments are secure, efficient, and compliant over time and aligned with business goals.
The core is the RAMP process:
- Ready: Establish the operating model and platform responsibilities
- Administer: Perform operations like deployments, incidents, change & access management
- Monitor: Track health, performance, security, and compliance
- Protect: Defend against threats, misconfigurations, and data loss
A key part of this phase is establishing a suitable operations model: centralized, decentralized, or shared. In enterprises, a shared model often works best—where a central platform team runs the infrastructure and sets standards, and workload teams manage their apps within defined guardrails.
Monitoring & Operational Data: Azure Monitor, Log Analytics, Application Insights, and Diagnostic Settings are the backbone of observability. Data flows are standardized via Azure Policies, collected through Data Collection Rules, and stored in centralized Log Analytics workspaces. Alerts are integrated with ITSM or SIEM tools (e.g., Microsoft Sentinel), supported by change tracking, agent health monitoring, and update management.
FinOps & Cost Optimization: Ongoing use of Azure Cost Management, budgets, reservations, savings plans, and Azure Hybrid Benefit is critical. Custom dashboards break down costs by tags, subscriptions, apps, and environments. Azure Advisor and Cost Management Recommendations offer optimization tips like shutting down idle VMs or selecting cost-efficient SKUs.
Change & Incident Management: All changes to infra and policies go through a CAB process via a central ITSM system. IaC and GitOps ensure full traceability. Incident workflows are triggered by Azure Alerts and integrated with ITSM/SIEM. Critical incidents can follow predefined runbooks or automation paths.
Security Monitoring & Compliance Tracking: Defender for Cloud detects threats and misconfigurations in real-time. Secure Score ratings are reviewed monthly by the CCoE. Regulatory dashboards (ISO 27001, NIST, CIS, GDPR) track compliance status. Policy violations or control failures trigger automated actions—e.g., tickets, access reviews, or governance board escalations.
Governance Iteration & Benchmarking: CAF’s Governance Benchmark Tool helps regularly evaluate maturity. KPIs like policy coverage, access review rates, FinOps compliance, or incident recovery time guide continuous improvement. Benchmarks feed into a semiannual governance roadmap managed by the Cloud Center of Excellence.
A mature cloud management setup aligns tightly with the Well-Architected Framework, promoting security, compliance, operational excellence, cost optimization, and reliability.
This phase proves whether governance is not only implemented—but sustainably embedded, automated, and continuously improved.
Azure Governance Building Blocks (CAF)
Microsoft’s Cloud Adoption Framework recommends building scalable governance on these four pillars:
- Policies & Compliance (Azure Policy, Regulatory Blueprints)
- Security Baseline (Defender for Cloud, IAM, Conditional Access)
- Cost Control (Azure Cost Management, Budgets, Reservations)
- Roles, Responsibilities, Processes (Cloud Owner, CoE, Change Management)
Connecting to the Well-Architected Framework
The CAF governance building blocks align directly with the Microsoft Well-Architected Framework (WAF), which defines five pillars for robust cloud architecture:
- Cost Optimization
- Reliability
- Security
- Performance Efficiency
- Operational Excellence
Governance is the connective element across all five:
Cost Optimization: Tagging strategies, budgets, reservations, and FinOps roles ensure cost transparency and control.
Reliability: Azure Policies, deployment pipelines, and monitoring standards keep infrastructure consistent, reproducible, and resilient.
Security: RBAC, PIM, Conditional Access, and policy-based enforcement translate security standards into action.
Operational Excellence: Governance embeds responsibility, change control, and automation across the org—improving traceability and reducing errors.
Performance Efficiency: Policies can enforce only approved services/SKUs—e.g., blocking low-value VM types—to ensure efficient resource use.
Governance is not just a compliance tool—but a structural principle in every WAF pillar. The full value is realized when CAF and WAF are combined: CAF provides the methodology, WAF the technical reference—together, they enable operational excellence in Azure.
Conclusion
By combining the Cloud Adoption Framework and the Well-Architected Framework, you now have a solid foundation to build a compliant, secure, and scalable Azure environment.
But how do you translate these principles into target architectures, toolchains, and technical decisions?
That’s exactly where Part 2 of this blog series picks up. It will give you the practical knowledge to shape a future-proof Azure platform. In upcoming posts, we’ll explore concrete implementation examples and further governance-related topics.





